Analytics
B2B Service Surveillance
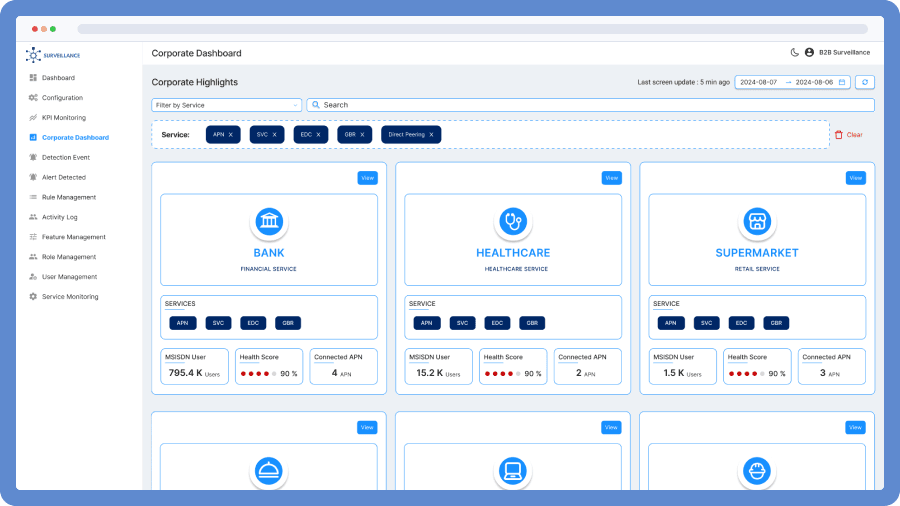
B2B Service Surveillance is a powerful platform designed to provide end-to-end surveillance for CSP B2B and B2B2X services, leveraging a service catalog-driven approach. By integrating real-time monitoring, advanced analytics, and AI-driven anomaly detection, it ensures comprehensive visibility across complex service ecosystems, enabling proactive issue resolution and seamless service assurance.
Real-Time Monitoring
Utilize a sophisticated surveillance platform that provides real-time insights into B2B infrastructure, enabling rapid incident response and proactive stakeholder communication.
AI-Driven Analytics
Leverage artificial intelligence to correlate data from various sources, enhancing the ability to detect anomalies and predict potential service disruptions.
Automated Incident Response
Implement automated workflows for incident management, significantly reducing Mean Time to Open (MTTO) and Mean Time to Resolve (MTTR) for service issues.
Comprehensive Reporting
Generate detailed reports on service performance, incident response times, and operational metrics, providing stakeholders with valuable insights.
Why Business Choose Tritronik B2B Service Surveillance

End-to-End Service Monitoring
Ensure complete oversight of CSP B2B and B2B2X services, tracking performance and detecting issues across the entire service lifecycle.

AI-Driven Anomaly Detection
Leverage artificial intelligence to correlate data from multiple sources, predicting and identifying potential service disruptions before they impact operations.

Service Catalog-Based Approach
Monitor services holistically using a structured service catalog, ensuring accurate tracking, streamlined operations, and clear service dependencies.

Proactive Incident Response
Enhance response times with automated alerts and intelligent workflows, ensuring minimal service disruptions and faster resolutions.

Comprehensive Reporting & Insights
Generate in-depth reports on service performance, incident handling, and operational efficiency, providing key stakeholders with actionable intelligence.

Data Security & Privacy
Ensure sensitive information is protected with advanced encryption, role-based access control, and compliance-ready protocols.